 |
English | ||||||
| Home page | Services | Past achievements | Contact | Site map |
|||
|---|---|---|---|---|---|---|---|
| Page d'accueil | Services | Réalisations précédentes | Contact | ||||
| Français | |||||||
| |||||||
|
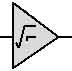
When constructing a conventional computer, the CNOT gate would not be sufficient, since the XOR gate is not a "universal logic gate" (due to the symmetrical behaviour of its two inputs). However, the quantum equivalent is not so constrained. Apart from the obvious extension of the idea to use a double-control-line CNOT gate, which only inverts the signal line if both of its control lines are at logic-1 (an idea that would work of conventional computing, too), there is the possibility of building √not gates. This is possible because the qubits are vectors (as opposed to bits, which are scalars). If two of these gates are applied to the signal, one after the other, it would yield the √not of the √not of the signal, namely the conventional logical NOT of the signal. |
Lastly, quantum processing is able to make use of the violation of the EPR paradox, so that discarded information that is routed out to dead-ends (decoherence lines), in a manner based on Fredkin-style processing of a reversible computer, are not really discarded at all, but have their information reflected back to the central parts of the logic circuit. Even more bizarrely, the quantum Zeno effect is proposed not only as a method of putting off the onset of decoherence (NS, 10-Nov-2007, p16), but can be used so that a computation is performed by a part of the algorithm's hardware even when that algorithm is never actually allowed to start running (NS, 25-Feb-2006, p21).
Wineland has demonstrated CNOT gates, built from positively charged beryllium ions, with the control qubit represented by the energy level of an electron orbiting the ion, and the signal qubit represented by the vibration of the ion within the trap (NS, 28-Sep-1996, p26). Separately, using several ions spaced out along a line, each held in place by strong electric and magnetic fields in the other two dimensions, he has demonstrated that vibration information can be passed along the line, like data along a data bus. This mechanism also serves to combat the onset of decoherence, with the information being passed on before the earlier parts decohere (NS, 08-Jun-2002, p24). Separately, he has also demonstrated the controlled, physical transfer of ions from one trap to another (NS, 06-Sep-2003, p21).
Barnes has demonstrated that non-decohered electrons can be successfully moved around, allowing them to be read in a region away from where the computation is conducted (NS, 24-Sep-2011, p22).
Other ideas for transferring quantum information from the output of one logic gate, to the input of one or more others, include Blinov's demonstration (NS, 13-Mar-2004, p17), of aiming a laser pulse at a logic-gate ion to make it emit a photon that carries a copy of the qubit's information. Moreover, if that information is subsequently manipulated, the change has been shown to be automatically imposed back on the transmitting ion.
Yao proposed a system (NS, 26-Nov-2005, p9) based on single electrons in superfluid liquid helium. Each electron repels the nearest atoms (about 700 of them), creating an "electron bubble". The electrons are held in appropriate places using a quadrupole trap structure, and a series of conducting rings to set up a pattern of peaks and valleys along the central linear region running along the middle between the four parallel conductors of the quadrupole. Because the system should be capable of handling 100 trapped electrons, and hence 100 qubits, and because they can be made to interact with each other, the technique offers some hope for making a fairly large quantum computer.
Wang, at Yale University, demonstrated an arrangement of two aluminium resonant cavities with a switchable interconnecting superconducting bridge (NS, 04-Jun-2016). By putting the switch in a superposition state of on and off, the cavities could be set in a state of resonating at two different frequencies. So as not to disturb the superposition state, the cavities were monitored for odd or even numbers of photons (individually, or as a single unit).
Using a macroscopic effect, Tsai built a silicon chip with two squares of aluminium, each one 0.1 micrometres wide (NS, 22-Feb-2003, p16). When cooled to below the superconducting threshold temperature, each square contained several Cooper pairs. When an electric field was applied, an extra Cooper pair could be added or removed, between the square and an adjacent reservoir, changing the qubit's state between 1 and 0, or to be put in a superposition of the two. A capacitor between the squares stopped electrons from tunnelling from one to the other, whilst allowing them to be close enough to feel each other's influence, and to become entangled. Superconducting loops are indeed showing great promise for implementing a quantum computer (NS, 10-Sep-2011, p18).
In fact, such macroscopic techniques raise the issue of whether this type of entanglement is "real" entanglement. This question is interesting, but not too important to the computer engineer, provided that the technique demonstratably performs a useful computation.
Indeed, the ability of structured objects to behave as quantum objects is well established in physics, anyway. For a start, protons behave as waves in double slit experiments just as readily as electrons and photons do, despite being composed of quarks; and streams of complete atoms behave as waves, too. Arndt and Zellinger have pushed this as far as showing it for C60 buckminster-fullerene molecules, and propose that it could be attempted with small viruses (NS, 15-May-2004, p30). This, in turn, leads to questions of the dividing line between quantum and classical behaviour, and the bridging between the two worlds by Schrödinger Cat devices (NS, 17-Mar-2007, p36; NS, 03-Aug-2013, p15). A system of a billion Cooper pairs acting as a single entity is, in fact, a simpler one than a system using a C60 buckminster-fullerene molecule.
Another experiment to probe at the boundary between quantum mechanical and classical behaviour involves the design of a quantum switch that can allow particles to pass or be blocked according to the state of a nearby qubit (NS, 22-Jun-2013, p16).
The use of knot theory, applied to braids of non-Abelian anyons, is described later on this page.
Memory
The spins of atomic nuclei can be used, rather than the states of their outer electrons, to represent qubits and might lead to qubits that are then better protected from decoherence from outside influences, whilst still being capable of being manipulated using strong magnetic fields.
Others have noted that the quantum states of phosphorus atoms are particularly long-lived, and resistant to decoherence. Clark, for example, demonstrated that the quantum state (stored as a charge) can be read out using sensitive single-electron transistors (NS, 30-Nov-2002, p21).
Quantum dots have also been much used as qubit memory structures, eventually to be organised as large lattices to implement large addressable memory devices. Each one is a speck of material (such as gold or semiconductor) just a few nanometres across that can confine a particle (notably an electron) in a space that is so small that its quantum behaviour dominates its classical behaviour. The quantum dots have to be arranged in regular arrays to make it possible to read each one, and techniques are mentioned below on how this can be achieved.
Rather than confining the particle in a physical object, another idea is to confine it at the interference fringes of two intersecting laser beams. The addressing of the individual atoms that are trapped at the intersections of such an optical lattice has been demonstrated, by two independent teams, at Garching and Harvard (NS, 21-Aug-2010, p14).
One idea allows the adding together the times of a series of events, as a sort of quantum stopwatch, so as to minimise the uncertainty in the measurement (NS, 02-Jun-2018, p13).
Input/Output
Interconnections between the individual logic gates has already been mentioned. The same sort of techniques for getting qubits to emit or absorb photons, and also the use of error correcting codes (NS, 07-Oct-2006, p12), also apply in the input/output function of the computer. IBM is investigating, with IARPA funding, the use of logical qubit arrays to achieve error detection and correction (NS, 12-Dec-2015, p7). Such successful strategies have indeed been demonstrated (NS, 04-Jun-2022, p21). There is a hope that quantum trajectory theory can be used to detect the onset of wave-function collapse, and thereby allow a signal to be injected that will cause the collapse to be averted (NS, 28-Mar-2020, p34).
One promising technique (NS, 16-Jun-2007, p16) involves the use of two Bose-Einstein Condensates: one at the sender location, and one at the receiver. By firing an extra atom into the sender BEC, it can only join the BEC if its extra energy (plus the information that it conveys) is emitted as light. Thanks to the physics of the BEC, this light is not emitted in all directions, but out in a single highly predictable direction. When the light arrives at the receiver BEC, its energy knocks out one of the atoms, and imparts it with all the quantum information that the original atom had contained. The technique has been dubbed 'classical teleportation', since the original and final atoms are not, themselves, constrained by classical behaviour, and can be conducted over arbitrarily long distances (the light can even be carried over optical fibres from the sender to the receiver).
A technique has been demonstrated (NS, 03-Sep-2005, p15) for allowing the information to be transferred between photons of different wavelengths, such as for systems that need to be probed at wavelengths around 800nm, and then to send the information on fibre optics at wavelengths of about 1300nm. A later scheme, too, demonstrated a method of onverting from one frequency to another, while preserving the information (NS, 19-Nov-2016, p17).
Researchers at the Swiss Federal Institute of Technology in Zurich have shown that two caesium atoms can be put in a Rydberg high-energy state, and form a single molecule with about a micron between the two atoms (NS, 03-Sep-2016, p14).
As well as serving as memory elements, quantum dots can also be used as probes, such as for chemical sensors, because the electrons' quantum states change when molecules bind to the dots. Similarly, since any ejected photon reveals the state of the particle that emitted it, qubits can be used as experimental probes to look inside atoms.
A scheme has been devised for preforming computation on publically available cloud servers, using cobits (qubits that can only be 0, 1 or in a 50:50 superposition) to encrypt the data from all but the client user (NS, 14-Feb-2015, p12).
The first real-world application of qubits was in the security of information transfer, of which quantum cryptography (NS, 02-Oct-1999, p28) and quantum key distribution (QKD) is the particular application, perhaps generated by a quantum random number generator (NS, 21-Apr-2018, p19), and even the issuing of quantum cheques (NS, 15-Jul-2017, p10). Since Bennett and Brassard's proposal in 1984, companies have been set up to commercialise it (NS, 25-May-2002, p22), with Singapore setting out to install the first nationwide network of secure quantum communication channels (NS, 10-Jan-2004, p34), and Vienna becoming the first city-wide system (NS, 18-Oct-2008, p24), with networks in China, which has been operating for some years (NS, 25-Sep-2021, p17) and in the United States subsequently improving on these (NS, 20-Sep-2014, p12). Zeilinger of the University of Vienna demonstrated transmission over a distance of 144km, using a laser source on a mountain on La Palma, in the Canary Islands, transmitting photon pairs to a 1-metre telescope at the Optical Ground Station of the European Space Agency on Tenerife (NS, 09-Jun-2007, p14). One demonstration involved communication using twisted light (NS, 19-Nov-2016, p9). The record for transmitting through seawater is 3m (NS, 02-Sep-2017). The possibility of setting up relay stations has been demonstrated (NS, 12-May-2018, p13) and of long distance optical fibre (NS, 29-May-2021, p36). The feasibility of satellite QKD has subsequently been demonstrated (NS, 29-Mar-2008, p23; NS, 28-Jun-2014, p15), boosted, perhaps, in the future by a technique of so-called twisted light (NS, 15-Nov-2014, p14). Subsequently, the Chinese Quantum Science Satellite (QUESS) has been placed in an orbit at an altitude of about 500km (NS, 27-Aug-2016, p16), and generating entangled pairs of photons, to transmit them to two ground stations a record-breaking 1203km apart, splitting the pair between the two sites (NS, 24-Jun-2017, p12). The eventual aim is to set up a QKD network between Hefei (China), Vienna (Austria), Munich (Germany) and Matera (Italy). Methods of sharing channels between multiple pairs of QKD exchanges has been demonstrated (NS, 22-Dec-2018, p14). Other milestones had been: 97km (NS, 19-May-2012, p4) by Jaun Yin of the University of Science and Technology of China in Hefei; 7km (NS, 30-Apr-2005, p11) by Pan Jian-Wai of the University of Science and Technology of China in Hefei; and, prior to that, 600m by Zeilinger (NS, 28-Jun-2003, p15) across the River Danube. QKD has also been demonstrated from air-to-ground, from an aeroplane flying at an altitude of 20km and a speed of 300km/hr (NS, 15-Sep-2012, p10); and air-to-air between two drones 1km apart (NS, 23-Jan-2021, p18). The delayed-decision double-slit experiment has been demonstrated over the 3500km distance of a transmission to a satellite and back (NS, 04-Nov-2017, p12). The University of Bristol has demonstrated a network, using multiplexing entanglement, that allows from 50 to 100 users to share a quantum network for QKD (NS, 12-Sep-2020, p21).
A security mechanism has been demonstrated using zero-knowledge proof (ZKP) and the constraint of the speed of light (NS, 13-Nov-2021, p20).
A proposal has been made to implement a more Enigma code like system using qubits (NS, 13-Jul-2013, p11).
A totally different type of processing has been demonstrated, called boson sampling (NS, 12-Dec-2020, p18) but, for the present, has few applications other than as a random number generator, such as for QKD.
One of the strengths of quantum cryptography is that any attempt to intercept the encrypted message by the eavesdropper, Eve, can be detected by Alice or Bob. However, in the real world, there are problems with the technology sometimes (often) spitting out duplicates of the information, thereby undermining this facility. Also, there is even evidence that the Eve might be able to extract information from the entangled photons, after all, without collapsing the wave function (NS, 12-May-2007, p32). Bell's inequality can be adapted to work with detecting eavesdroppers in a network of more than two users (NS, 20-Jan-2018, p9). The teleportation of information from Alice to Charlie without strictly passing through Bob has been demonstrated (NS, 04-Jun-2022, p23).
As with all encryption systems, even quantum communications have weaknesses. At the very least, there are inevitably fallible human users of the system. But, also, there is the interface between the classical world, and the quantum communication channel, which turns out, indeed, to be vulnerable to potential hackers (NS, 22-Oct-2011, p44; NS, 29-Oct-2005, p30; NS, 29-Nov-2003, p24). Wehner, at Delft University, has demonstrated a technique for device-independent cryptography, called "entanglement swapping", that uses the Bell test to tighten up on the locality loop-hole (NS, 31-Oct-2015, p36).
Somewhat out of context, here, methods have been demonstrated that work under "encryption(A op B)=encryption(A) op' encryption(B)". That is, a third-party can safely be given access to an encrypted database, perform operations on it, and to ask the owner to decrypt the result (NS, 09-Apr-2022, p36).
Manufacturing Techniques
Single Particle Traps
As noted earlier, qubits can be represented using any multi-state quantum variable, such as spin, polarisation, charge, vibration, or energy level. It can be hosted by any quantum particle, notably a photon, an electron, an atomic nucleus, or a complete atom, molecule or ion.
If the qubit is hosted by an electron, nucleus, atom or ion, the host needs to be held in place in a suitably designed trap. Many of the experiments to date, therefore, involve trapping a single atom in a specially designed structure (such as a quantum dot), or a single electron in an especially unique orbital of a conventional atom.
Specially chosen molecules, such as chloroform (CHCl3), have been used to implement CNOT logic gates, with the resonant frequency for flipping the spin of the carbon nucleus being slightly altered depending on the state of the spin of the hydrogen nucleus. IBM's liquid NMR machine was used to entangle seven qubits. Unfortunately, the technique does not appear to generalise, with the signal becoming undetectable beyond about a dozen qubits on each molecule. This, even when using of the order of 6x1023 copies of each molecule, dissolved in a liquid solvent, to multiply up the signal (NS, 08-Jun-2002, p24). One possibility is that ion trap qubits can be driven by magnetic fields instead of by laser, so making the idea more readily scalable (NS, 10-Dec-2016, p7).
Single atoms of phosphorus, barium, carbon or hydrogen have been used. These can be trapped, one atom at a time, in the cage-like structure of a Buckminsterfullerene molecule, or on a silicon substrate, or within the silicon lattice. A team at the University of Maryland have implemented an externally programmable 5-qubit ytterbium-ion device (NS, 13-Aug-2016, p14).
Clark's device was fabricated by focussing a high-energy beam of phosphorus atoms on to a silicon chip (NS, 30-Nov-2002, p21), and Kane's method (NS, 13-Jan-2001, p14) involved positioning the phosphorus atoms ions while they were floated on a thin film of superfluid helium with an electric field applied – removing the electric field subsequently causing to atoms to sink through the film to the silicon substrate, where they bonded.
One way to make quantum dots is to spray indium arsenide molecules on a gallium arsenide surface and to allow the molecules to clump together into droplets. As a further development, Kotthaus (NS, 18-Mar-2000, p18) found that, if they were coated with a layer of gallium arsenide as they formed, the droplets changed shape, forming ring-shaped structures (like a deep volcano cone). Single electrons then spontaneously circulated round the ring when a large 8T magnetic field was applied.
Linke demonstrated many interesting effects occurring in strings of triangular quantum dots (NS, 22-Jan-2000, p28). By applying an external alternating electric field, electrons showed a bias to flowing from triangle points to the body of the next triangle, or vice versa, depending on the voltage and frequency. This could be used to extract DC energy from the alternating field, to power a device; or it could be engineered to form a logic gate, conditionally switching the flow of electrons, along with any quantum information that they carry. Moreover, Sheilds has achieved this using conventional silicon lithography (NS, 14-Jan-2006, p19).
Encoded qubits on the spin of a few phosphorus atoms embedded in a matrix of silicon, were trapped for over three minutes (NS, 16-Jun-2012, p19). Another technique involves manouvering single atoms of sodium and cesium together, using three laser beams, and encouraging them to form a loose chemical bond together; the spinning molecule turns out to be very robust against the effects of surrounding thermal noise (NS, 21-Apr-2018, p15)
One disadvatage of using a trapped ion to implement each qubit is that the ions have to be kept isolated. By using neutral caesium atoms, instead, excited and maneuvered in place by lasers, is that they can be configured to interact according to the given algorithm, and reconfigured for the next one (NS, 22-Jan-2022, p9).
Coherent bulk materials
Qubits can also be hosted in a bulk material that has been made to behave as a unified, single object, as is the case in superconductors, superfluids and Bose-Einstein Condensates. By cooling down the material to near absolute zero temperatures, the momentum of each one becomes so constrained that the uncertainty on its spacial extent becomes large, and the individual atoms blur together, to appear and behave as a single object. In a Bose-Einstein Condensate (BEC), entanglement has been taken to the extreme of forcing all the atoms into the same quantum state, so that they behave as an enormous single compound particle. That quantum state is, in fact, their lowest energy, or ground state. This has now also been demonstrated (NS, 08-May-2021, p15) for clouds of caesium molecules, rather than atoms
Less exotic techniques have also been demonstrated, though. One involves switching the currents in superconducting circuits in a relatively conventional way. One particular example proposes the use of superconducting dots (NS, 19-Sep-2009, p42). Even conventional capacitive devices have been used for storing the qubit information.
The main disadvantage of the multiple-particle approach, though, for representing qubits is that the whole qubit decoheres as soon as just one of its component particles does. The single particle approach, though, is almost certainly harder to construct. Moreover, there is a suggestion that mean-time-to-decoherence might scale inversely with the size of the qubit (NS, 25-Jun-2005, p18), down to about a microsecond. On the other hand, others argue the opposite, that the decoherence of individual qubits cannot be treated as independent events, and that it will never be possible to sustain quantum computation (NS, 02-Dec-2006, p17).
Dark State
Photons can become coupled with another particle, to form a polariton virtual particle, and can be made to behave as a rigid fluid (NS, 03-Nov-2018, p6).
Light travels slower in materials than it does in a vacuum. In water, it is slowed by 75%; in a vapour of rubidium atoms, it can be slowed to 8 m/s, and in a BEC, it can be slowed to 0.5 m/s (NS, 20-Feb-1999, p10). The ultimate achievement is to bring it to a halt, in the so-called dark state.
Hau created a cloud of sodium atoms, and cooled it down to the atoms' ground state, to create a BEC (NS, 22-May-2004, p32, from which the following paragraphs are paraphrased). Two laser beams are then fired at the cloud:
- The coupling beam
- with a photon energy equal to the difference between two of the many higher energy levels of the atoms
- The signal beam
- with a photon energy equal to the difference between the ground state and the upper of the two chosen higher levels
The coupling beam nudges the gas atoms into a dark state in which their electrons are unable to jump up to higher energy levels. This means that the atoms cannot absorb light of that particular wavelength, so when the signal beam enters the gas, it interacts with the spin of the electrons instead. This is what absorbs the energy (and hence the information) from the beam, and slows the pulse down.
At certain combinations of amplitude and phase, the two beams interfere destructively, and no absorption occurs in the cloud. However, the photons and atoms still become entangled, and the cloud ends up with a very high refractive index. As a result, the original pulse length of the signal beam is reduced from kilometres to a few micrometres.
By gradually reducing the amplitude of the coupling beam, the refractive index is increased further, with energy being extracted from the photon stream by the entangled atoms. Ultimately, when the power of the coupling beam reaches zero, the speed of light approaches zero, and the signal beam enters the so-called "dark state". Heinze at the University of Darmstadt has managed to hold light in such a state for over a minute (NS, 27-Jul-2013, p19).
By using two coupling beams instead of one, regions of constructive and destructive interference can be created, with islands of constructive interference surrounded by regions where the speed of light has been reduced to zero. The travelling signal beam is trapped as a standing wave on these islands. A pulse from a second signal beam, which also then goes into the dark state, will then cause interactions to occur between the two sets of photons, altering the phase and intensity of the standing wave, and hence the information content.
This technique offers great promise in at least three application areas:
- As a means of probing the internal structure of the atom
- (since the entangled photons exchange quantum information with the atoms)
- As a means of level-restoration in fibre optics
- (allowing the signal to be amplified, while leaving the noise behind)
- As a means of making the photons interact
- (which they do not normally do, and so presents an important development for quantum computer wiring, and quantum computer processing)
Meanwhile, Lukin and Walsworth have demonstrated a similar slowing of light when shone through a warm cloud of rubidium atoms (NS, 27-Jan-2001, p4) and by Howell through another hot cloud of caesium atoms (NS, 10-Feb-2007, p11). This has possible applications for memory devices, for storing the information content of light directly, without having to convert it first to electronics. Ryu and Boshier even propose the movement of such atoms as the information carriers in circuits (for atomics) in place of that of electrons (for electronics) (NS, 15-Nov-2014, p16).
For processing, the use of an optical lattice for implementing quantum logic gates has been demonstrated (NS, 28-Jul-2007, p19). This involves firing three lasers at a volume of ultra-cold rubidium atoms, to set up interference fringes in three dimensions. Although this sounds similar to the idea of using the dark state of light, the actual idea demonstrated was a much simpler one: pairs of atoms in the dark fringes can be made to become entangled, and can be manipulated by changing the polarisation of the lasers with time.
For the techniques that use bulk material, rather than individually trapped atoms, the engineering structure is imposed upon the device by a set of externally applied beams. This is not too dissimilar the current use of photolithography to impose structure on monolithic crystals of silicon. Indeed, Greentree has proposed the use of diamond, glass or plastic as the substrate, with regular dislocations for holding individual caesium atoms, somewhat akin to the technique of doping silicon with impurity atoms (NS, 13-Jan-2007, p42). Hemmer and Turukhin have demonstrated the use of a substrate of yttrium silicate doped with praseodymium ions (NS, 12-Jan-2002, p19).
It should be noted, though, that microelectronics uses a static structure, set up at fabrication time, formed by a beam that is modified by a complexly patterned mask: while the dark-state and optical lattice ideas use the two beams to set up a simpler structure, in real time. The use of masks, though, might still be a possibility for exposing selected areas, and might, of course, also provide slits to help in the generation of a complicated pattern of fringes. Moreover, being a dynamically set-up structure can be its major strength: it could allow the hardware to be reconfigured as the computation progresses, allowing a small amount of hardware to be multiplexed for use on a large amount of computation (in a style not unlike the ANN FPGAs of Daedalus, NS, 28-Sep-1972, p616). Indeed, it is not just the patterns generated by the laser beams that can be reconfigured during the computation, but the properties of the underlying matter, too (NS, 09-Feb-2008, p44).
Topological quantum computing
The use of knot theory (NS, 18-Oct-2008, p32) has been proposed as a mechanism for quantum computing (NS, 24-Jan-2004, p30). Moving quantum particles around one another can be considered as constituting a braid, when plotted out in space-time, where the strands represent the positional histories of the individual particles. Since any given knot can be specified in terms of a string of 1s and 0s, it can, conversely, be considered to act as a memory store containing that number (as, indeed, the ancient Incas discovered). Moreover, since any given algorithm can be expressed as an integer (as in Turing's description numbers and computable numbers), each knot can also be considered to code for a particular computation. Moreover, the method of storing the information promises to be more robust than the conventional decoherence-prone representations of qubits using spin, charge, energy or polarisation. The idea does, though, hinge on the use of one particular type of particle, called a "non-Abelian anyon", and this has yet to be shown to exist in nature.
The signs are not unhopeful, though (NS, 04-Oct-2008, p40): by passing an electric current along a length of two-dimensional crystal lattice that is cooled to a very low temperature, and constricting the width of the channel by a magnetic field, the body of moving electrons behaves as though there are particles with anyon-like properties flowing along one edge of the channel, and back along the other edge. Under the right combination of conditions (putting the electrons in a quantum Hall state with a filling factor that is the ratio of two suitable integers) non-Abelian anyons do indeed appear to be created, and hence to offer hope of being usable for quantum computing. A theory to explain this observed behaviour appears to be tractable, too (NS, 09-Feb-2019, p38).
Alternatively, perhaps string-net liquids could be used for the braiding (NS, 17-Mar-2007, p8), and might even be observable in a real crystal such as herbertsmithite.
Road to commercial quantum computers
Eventually, quantum computing will be required to design subsequent quantum computers (NS, 25-Sep-2021, p11) but, in general, quantum computers will only be useful on particular classes of problems, as implied in the section on software; for conventional algorithms, digital electronic computers will continue to be the most ideally suited. A summary of the state of quantum computer development at the end of 2021 can be found in (NS, 01-Jan-2022, p15). For strategic reasons, the race has taken on a nationalistic tone (NS, 02-Oct-2021, p20).
Even small quantum computations can continue to be executed perfectly adequately on conventional computing hardware. At first, the threshold between small and big was assumed be around 50 qubits, as this was considered to be the limit of the size of computation beyond which a conventional super-computer would find it impossible to execute in the availble time. More precisely, the quantum supremacy threshold was considered to be a problem involving 48 qubits to a circuit depth of 40, though this is now revised to 49 qubits to a circuit depth of 48 (NS, 18-Aug-2018, p10). However, quantum hardware simulators are now up to simulating 53 qubits (NS, 09-Dec-2017, p14), and new algorithmic techniques now push this threshold to 56 qubits (NS, 28-Oct-2017, p12).
D-Wave of Burnaby, Canada, is the first commercial venture to claim to sell a quantum computer (NS, 16-Mar-2013, p8), selling an adiabatic quantum computer to Lockheed Martin to run simulated annealing algorithms (NS, 04-Jun-2011, p6). Benchmark tests were run that compare it (favourably) with a high-end PC (NS, 18-May-2013, p4). Google then became the second customer (NS, 25-May-2013, p4), with an improved version of the machine for fast database search algorithms, using quantum annealing (NS, 06-Dec-2014, p10), and for designing software and blink detector training for the Glass (NS, 19-Oct-2013, p5); but the machine initially returned less favourable test results (NS, 25-Jan-2014, p11), and in any case is comparing the machine against conventional computers running a simulated annealing algorithm that is unrepresentative of their normal work (NS, 19-Dec-2015, p12). Further contested performance results continue to follow the machine (NS, 29-Aug-2015, p6). Meanwhile, a third customer for D-Wave is the US Los Alamos National Laboratory (NS, 21-Nov-2015, p7). D-wave's Advantage has 5000 qubits, but is still only a bespoke hardware (NS, 10-Oct-2020, p17).
Morello, at the University of New South Wales, advocates the use of silicon (NS, 16-Sep-2017, p9), following on from Kane's method for positioning phosphorus atoms ions on a silicon substrate (NS, 13-Jan-2001, p14). Simmons is building single-phosphorous atom transistors in close proximity, each one holding a single qubit, and is aiming at building a 10-qubit system by 2022, and above that, up to 100 qubits, by 2027 (NS, 27-Oct-2018, p42).
The IBM Quantum Experience computer is a 5-qubit superconductor-based device (running at 0.015K) available to users over the internet (NS, 13-Aug-2016, p14). IBM later announced that this could now be replaced by a 20-qubit machine (NS, 18-Nov-2017, p7), with the prospect of a prototype for a 50-qubit machine after that, each one able to sustain computations for at least 90 microseconds. Their Eagle project has 127 qubits, but is intended to be scaled further to their 400-qubit, and later 1000-qubit Condor project (NS, 20-Nov-2021, p7).
Meanwhile, Google began to design its own 50-qubit machine (NS, 13-Sep-2014, p7), named the Supremacy Project (NS, 03-Sep-2016, p8), as a proof-of-principle spur to creating the first commercially useful machines (NS, 23-Dec-2017, p39). A 9-qubit version was able to demonstrate a quantum-sampling algorithm (NS, 07-Oct-2017, p12). They reported success on a 20-qubit version, with the intension of extending to 49-qubits (NS, 01-Jul-2017, p6), and quickly on to the 72-qubit Bristlecone version of the original 9-qubit machine (NS, 10-Mar-2018, p5). They reported success, with a 53-qubit version, called Sycamore, that was able to judge the randomness of a given input stream in 3.33 minutes, and that would have taken a Summit conventional supercomputer 10000 years (or at least 2.5 days) to compute (NS, 02-Nov-2019, p6; NS, 05-Oct-2019, p15; NS, 28-Sep-2019, p5). The next aim is to simulate quantum chemical behaviour with a quantum computer (NS, 21-Dec-2019, p10), though there are others who question as to whether a practical achievement of 'quantum advantage' by these specialised computers will be made any time soon (NS, 11-Jan-2020, p10) not least since more conventional optical computing can be ramped up to solve many types of optimistaion problem (p13 same issue). A mathematical framework has been developed for analysing algorithms to proport to lead to quantum advantage (NS, 18-Jun-2022, p19).
Google's Supremacy Project uses superconductor-on-insulator technology to implement the qubits. Intel also are investigating the use of superconducting elements as part of their long-term research, but are focused more on the use of single-electron silicon transistors for the present, with an aim to scaling up quickly from the 50-qubit level to millions or billions of elements (NS, 05-Jan-2019, p12).
IonQ's product only has 32 qubits, implemented using trapped ions that are manipulated by lasers, but claims to have a volumn-metric of 4 million, beating the previous record-holder with a volume-metric of 64 (NS, 10-Oct-2020, p17). This metric takes into account the error-rate on the qubits.
The Centre for Nanoscience and Quantum Information, at the University of Bristol, has become the first establishment to make quantum computing available to the public, via the internet (NS, 30-Nov-2013, p10). Indeed, the UK aims, though the Quantum UK programme, by 2020, to have built a parallel network of twenty 20-qubit quantum computers (Q20:20) and to have a Bristol-London-Cambridge QKD network (NS, 17-Oct-2015, p10). Amazon Braket (NS, 07-Dec-2019, p8) is an internet interface to provide access to machines at D-Wave, IonQ, and Rigetti Computing (using superconductor circuits). Honeywell, too, plans to make hardware available over the internet, consisting of four robustly-coherent, dynamically-reconfigurable, trapped-ion qubits (NS, 07-Mar-2020, p12). Reilly, of a startup called Turing, is investigating the use of diamond (NS, 16-Sep-2017, p9). The Borealis computer is made publicly available on the internet (NS, 11-Jun-2022, p18) using boson sampling, but separating them in time (thereby economising on the hardware) as opposed to in space, as had been done by the Jiuzhang 113-photon machine from USTC (both machines having demonstrated quantum advantage/supremacy).
Further implications
Inevitably, there are implications on our theories on the working of the human mind, such as those involving Posner clusters or microtubules (NS, 05-Dec-2015, p28), and on those for physics, and consequently even on towards a theory of everything.
map